Proposal Funded by EPSRC Programmable Networks Programme
GR/R31409/01
PolyNet: Policy Based Management of Adaptive Networks
Morris Sloman, Wayne Luk, Emil Lupu, Naranker Dulay
Imperial College, Department of Computing, 180 Queen’s Gate, London SW7 2 BZ
m.sloman, w.luk, e.c.lupu, n.dulay @doc.ic.ac.uk
25 Oct 2000
1 Motivation
The convergence between Telecommunications and Computing, together with the need to support mobile computing systems, requires new dynamically programmable network architectures that support fast service creation and resource management through a combination of network aware applications and application aware networks. Adaptive networks must support rapid deployment of customised services tailored for potentially mobile, corporate and individual users. The proposed research will explore the interaction between adaptation within network-aware applications, application-aware networks and programmable network hardware using the Ponder framework for specifying management and security policies.
The software required to support adaptive networks will require dynamic installation of cooperating software components on network resources to support QoS (Quality of Service) management, caching, persistence and security. Programmable components can include management scripts downloaded to perform diagnostics, or mobile agents which migrate around the network to support mobile users. Reconfigurable hardware based on Field Programmable Gate Array (FPGA) devices are needed to adapt the "fastpath" behaviour of routers or firewalls for high-speed, gigabit network interconnect. This environment will be constantly changing to accommodate new services, new technology, changes in organisational structure and procedures, and evolving application requirements; so it should be possible to change the behaviour of components, from software objects to FPGA configuration bitstreams, via downloadable policies.
Policies are rules governing the choices in behaviour of a system. Authorisation policies are used to define what services or resources a subject (management agent, user or role) can access. Obligation policies are event triggered condition-action rules which can be used to define the conditions for reserving network resources, changing queuing strategy, loading code onto a router, or reconfiguring an FPGA for higher performance but with reduced error correction capability. A policy-enabled application may interpret policies to adapt to requirements of specific users, such as what information to filter when bandwidth or device capabilities are limited. However some of the application specific policies may have to be enforced within the network. Thus policy-enabled applications need to be able to transfer policies to policy-based programmable networks. Similarly, the network may need to pass policies to be interpreted by the application for more efficient adaptation, for instance related to caching or monitoring of application specific components. The main objective of this project will be to investigate the interaction between policy aware applications and policy based networks across multiple levels of adaptability as described below.
There are many different approaches to supporting programmability of networks, including active IP packets which carry code; mobile agents which carry state information and code to perform configuration functions in routers and in FPGAs; and provision of a management interface on network components for downloading scripts or code for FPGA configurations. The various approaches can be used to perform complementary functions, although there is some overlap between them as a particular functionality could be implemented using more than one approach. In addition, these are all very powerful facilities which can drastically affect the normal working of the network, so would require Ponder authorisation policies to define who can initiate these techniques and what they can do within the network components.
This project will investigate the use of policies to support adaptability at three levels: (i) within network-aware applications, (ii) within application-aware networks, and (iii) at the hardware level to support adaptability in the packet forwarding "fastpath" of network elements. We will make use of the Ponder Policy Specification Language developed at Imperial College which supports both management and security policy specification, to investigate how to use policies to manage QoS, how to provide application-specific routing configurations such as multiway multicast, and to define who can program specific components and what programming operations they can access [44]. Although other groups are looking at policy based network management or configurable network processors based on FPGAs, we are not aware of any other work on how the above three levels of programmability can interact using policy. We will develop a simple collaborative application involving users with variable capability workstations and communication links (including mobile and/or wireless), supported by an experimental network facility as a means of evaluating both functionality and performance. This will also enable us to evaluate Ponder as a language for programming networks at various levels of abstraction, and hence refine the language.
2 The Ponder Policy Framework
Ponder is an object-oriented, declarative language developed at Imperial College for specifying management and security policies [10]. For example, the following authorisation policy with the name bwalloc permits the Agroup to perform the action of setting up a videoconference with bandwidth of 4 Mb/s and priority of 3 to the BGroup in New York or the Dgroup in Boston between 16.00 and 18.00 daily.
inst auth+ bwalloc {
subject Agroup; target BGroupNY + DGroupBoston;
action videoconf (bw=4, priority=3);
when time.between (1600, 1800); }
The following obligation policy type named videoSetUp, takes two parameters – a subject which interprets the policy and a target on which the action to reserve bandwidth is performed, when an event is received for a videoRequest with the requested bandwidth bw as a parameter. A constraint defines that the reservation will only take place if the allocated bandwidth plus the request is less than a maximum allowed bandwidth. It is assumed that the allocated and maximum bandwidth are variables held within the subject. Two instances of the policy are then created for different gateway subjects and router targets.
type oblig videoSetUp (subject s; target t;) {
on videoRequest (bw);
do t.bwreserve (bw);
when ((s.allocatedbw + bw) < s.maxbw); }inst USvideoSetUP = videoSetUp (gateways/USgateway, routers/USedgeRouter);
UKvideoSetUP = videoSetUp (gateways/UKgateway, routers/UKedgeRouter);
Ponder also supports grouping of policies into roles related to positions in organisations or the set of policies applying to a particular network component. Management structures can be defined as configurations of roles with policies applying to relationships between roles for organisational units such as departments or buildings. Inheritance permits specialisation of existing policy specifications for different environments. Ponder also allows complex actions to be implemented by dynamically loaded scripts within the subject policy interpreter, which would support a management interface type of network programmability for adding new functionality to the router. Details of the Ponder language are described in [10] [11]. We have specified various access-control policies, meta-policies, and composition of policies in Ponder. Although we have compiled some Ponder descriptions into software such as firewall rules [2], we have not mapped these onto real routers or FPGA-based platforms. We are requesting resources to set up an experimental network as a framework for implementation, validation and experimentation with policies in routers, firewalls and gateways. Vendors have offered FPGAs and commercial routers and switches. There are a number of problems to be solved for communicating policies between applications and network components. For example, Ponder has explicit subject and targets defined in terms of domains in a policy rule. However the application may not know about domains defined within the network infrastructure or even the specific actions supported by routers. There will need to be a transformation of the policies provided by the application into those which the network can understand.
3 Reconfigurable hardware design
Network processors have to satisfy two demands: supporting the need for increasing bandwidth, and delivering new features such as the capability to implement QoS and service level agreement monitoring. FPGAs are suitable for building network processors, since they combine programmability of software with a performance approaching that of custom hardware. We have developed an automatic way [50] of mapping firewall rules into a high level language known as Handel-C [12], which can then be compiled into FPGA bitstreams. Despite relatively little effort on optimisation, our prototype packet filter for a Xilinx Virtex XCV1000 FPGA running at 40MHz is 60 times faster than a software version running on a 700MHz Pentium PC.
We aim to extend this work in three directions. First, we shall investigate efficient implementations for security and QoS management in adaptive networks, based on our research on parametrised hardware libraries [29] and pipeline vectorisation techniques [49]. Second, we shall develop compilation schemes for mapping Ponder descriptions into hardware implementations. This work should benefit from related research on mapping Ponder to firewall rules [2], and on supporting hardware acceleration of software frameworks such as Matlab for signal processing [7] and OpenGL for graphics [46]. Third, we shall explore the use of reconfigurable hardware for fastpath adaptation in network elements at run time. We have developed compile-time [42] and run-time [41] techniques for such reconfigurable designs, and will specialise these techniques for networking applications. Case studies will be implemented using the experimental network (see section 3) to evaluate the effectiveness and potential of our approach.
The proposed research will benefit from interactions with related projects sponsored by industry. Celoxica is supporting work on reconfigurable hardware design using Handel-C for a variety of applications, including graphics, imaging, encryption and data compression. Research on application-programming interfaces to support hardware acceleration of well-known software tools, such as Matlab [7], Adobe Premiere [17] and OpenGL [46], has been supported by Celoxica, HP Labs, Sony and Xilinx. We have also developed a hardware platform, in collaboration with Blue Wave Systems, for wireless telecommunication and signal intelligence (see http://www.bluews.com/products/project.cgi?175). The experience gained from these projects will be useful in developing techniques, tools and testbeds for the proposed FPGA-based network processors.
5 Research objectives and research issues
The overall objective is to evaluate the Ponder Policy Specification language as a means of specifying and implementing both security and management policies for adaptive networks. The specific objectives of this proposal are:
To develop techniques and interfaces for interaction between policy-based applications and policy-enabled networks in order to support dynamic adaptation;
To investigate the use of Ponder management and security policies as a means of ‘programming’ network components such as routers, firewalls or dynamic proxy servers within the network for applications requiring adaptive networks;
To extend the Ponder compiler for IETF/DMTF information models and schema to demonstrate that Ponder is a suitable language for specifying the many different types of policies being defined within these standards groups;
To provide techniques and tools for the use of Ponder in producing FPGA-based network processors, particularly implementations involving run-time reconfiguration of hardware components;
To set up an experimental testbed for policy based management, and develop a simple policy aware application as a means of evaluating the application-network policy interface and the use of reconfigurable FPGAs for fastpath adaptation in network elements.
The research issues to be addressed by this project include:
How should policies be communicated between network elements and application components? This includes the representation of policies and transformation between the semantics understood by the various elements.
Are there particular methods or design patterns for building policy aware applications?
Can we use policies to manage the deployment of policies and hence support adaptive policies which change according to network conditions?
What are the limitations of Ponder in terms of expressiveness and performance for defining policies as a means of ‘programming’ network elements such as routers and FPGAs to manage quality of service?
How do we specify constraints in order to prevent conflicts within a set of policies for a particular network component or across a set of cooperating components?
Can patterns be determined for refining high-level policies into the implementable policies needed for programmable networks?
How do we exploit reconfigurable hardware in high-performance routers and switches for adaptive networks?
How do we map a policy-based specification into implementations involving reconfigurable hardware and software?
What are the trade-offs in cost, performance, flexibility and development time between various software and hardware-assisted implementations?
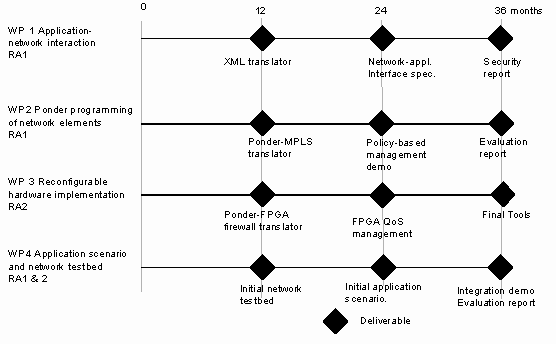
5 Work Packages
5.1 WP1: Interaction between policy-aware applications and policy-based networks
The two main issues here are how do we represent policies, and how do we map the policies which are meaningful to the application onto those appropriate for network components. We will investigate XML as the means of representing policies, but the IETF are using X500 directory schema to define policies for storage in a directory server [35]. It is possible that a form of a simplified service level agreement (SLA) whereby an application requests a particular class of service may be a suitable interface for some applications related to QoS. However this may not be adequate for other applications, such as mobile computing, where it is necessary to set up adapters within the network to perform compression, filtering or information transformations. It is necessary to determine whether policies, possibly generated from different applications, conflict. We are investigating the use of the Object Constraint Language [37] as a means of specifying what is a conflict between policies and then using this to detect conflicts within a set of policies, within the SecPol project. We will build upon work within the BT Alpine project which is investigating the use of proxylets which are loaded as required into servers within the network to perform adaptation at the application layer. We are also investigating the use of policies within SLAs and refinement of these into implementable policies within two other EPSRC projects SecPol and Ponds. This workpackage will investigate the use of Ponder to specify what resources or services applications can access within the network, and what actions are permitted for different network programming techniques such as active networks or management by delegation. We are also collaborating with University of Bologna on specifying policies related to mobile agents which will map onto the security support within Java [7] and when to trigger agent migration [9].
Deliverables:
Month 12: Ponder to XML translator.
Month 24: Network-application interface specification and required transformation.
Month 36: Report on Security for Programmable Networks.
5.2 WP2: Ponder Based Programming of Network Elements
We have been experimenting with translating Ponder into Firewall rules for controlling access, although there are some challenges with mapping Ponder constraints (e.g. for time based policies) into the mechanisms supported by firewalls. We would like to focus on Multi-protocol Label switching (MPLS) as a potentially important mechanism within routers and switches for managing QoS and defining flows for multi-media applications. The main issues are to determine what can be specified and implemented as policies and where scripts are needed to provide the required adaptability. We intend to evaluate the performance implications of executing policies on routers and determine what types of policies are more suitable for execution in management components. We intend to experiment with Linux-PC based routers as well as commercial routers or switches which may have more limited programming capabilities requiring external policy decision making components.
A student has been investigating the mapping of Ponder to the IETF X500 Policy schema [35], although this is rather verbose and not easy to understand. The DMTF CIM model [12] may be a better target, as it provides a higher level object-oriented information model. We anticipate that this work, which essentially requires back-ends to the Ponder policy compiler, can be done by undergraduate and MSc student projects, as it is reasonably independent of the other work packages. The Cisco funded research student would work on Policy dissemination for large-scale systems.
Deliverables:
Month 12: Initial translator of Ponder onto MPLS or other suitable router control interface.
Month 24: Policy Based Management Demonstration.
Month 36: Evaluation report.
5.3 WP3: Techniques and Tools for Reconfigurable Hardware Implementations
This workpackage explores the means of mapping Ponder specifications into implementations involving hardware and software, and provides tools for analysing and synthesising such implementations. There are already two simple and currently independent prototype tools: one translating a subset of Ponder into firewall rules [2], and the other compiling firewall rules into hardware descriptions [50]. We shall explore compilation schemes and compilers based on the experience from these tools and other relevant tools [49] to improve their scope and efficiency. For instance, efficient and modular components for packet filtering will be developed, building upon our work on parametrised hardware libraries [29], hardware hashing techniques [40] and related work on reconfigurable content-addressable memories [14]. Another area of interest is to extend our hardware compilation scheme for Ponder to include, for instance, QoS management using traffic shaping strategies.
We shall also investigate the use of Ponder in producing run-time reconfigurable implementations for adaptive networks to support both security and QoS management. This can be supported by local scripts, invoked by Ponder obligation policies, that reconfigure the appropriate FPGA components. A framework for producing run-time environments will be developed to facilitate rapid hardware reconfiguration, extending our work on architectures for analysing and synthesising circuits at run time [28][41][42]. The framework will enable us to study various trade-offs, such as reconfiguration time versus efficiency of the reconfigured circuit, so that the impact on QoS and on other resource and performance aspects can be assessed.
Deliverables:
Month 12: Initial Ponder compiler for FPGA-based firewall implementation.
Month 24: FPGA based QoS Management support and refined compilers.
Month 36: Evaluation report.
5.4 WP4: Application Scenario and Experimental Testbed
A simple collaborative application with video conferencing support would provide a suitable application for which user-specific policies can be defined. For example, some users might have wireless based lap-tops and define preferences on how to deal with low bandwidth links or which media streams should have priority. There is a need to support simultaneous multicast trees for these applications, and this changes as users join and leave the collaborative group.
We will set up a programmable network testbed consisting of 3 Linux-PC based routers, and some commercial routers or switches. We hope to be able to install policy components on routers in the sites of the partners in the Alpine project (Lancaster, UCL, Sussex, BT and UTS Sydney) which would permit edge router type controls across a wide area network. The testbed will require artificial traffic generators for evaluation of QoS policies. The testbed will include FPGA-based platforms to allow experiments involving reconfigurable hardware, such as supporting fastpath adaptation. Our plan is to use two RC1000-PP systems, with which we are familiar [46], either separately as two network nodes, or jointly as a single node with the boards connected together by a ribbon cable; we have already developed such a cable for an earlier design. The RC1000-PPs should be populated with the latest FPGAs, such as Xilinx XCV2000 devices. Since hardware platforms are changing rapidly, we shall investigate other hardware platforms before purchase to ensure that we get the best deal for the project. This set up will enable us to evaluate how easy it is to write QoS and other management policies in Ponder and map them onto heterogeneous devices (e.g. compared to IETF policies or CLI scripts for routers). We need to evaluate the performance of the Ponder policy interpreter and experiment with various strategies for interpreting policies. The testbed will also enable us to experiment with Ponder as a means of programming firewall policies. Furthermore, the testbed will provide a vehicle for exploring trade-offs in cost, performance, flexibility and development time between various software and hardware-assisted implementations.
Deliverables:
Month 12: Testbed installed with traffic generators.
Month 24: Application scenario with policy interface implemented.
Month 36: Integrated Application-network policy interaction demonstration. Evaluation report.
7 Workplan

7 Related Work
At Imperial College on Policy and Reconfigurable Hardware Design
BT funded Alpine Project Application Level Programmable Inter-Network Environment includes Imperial College, University College London, Lancaster, Sussex Universities and University of Technology Sydney. Imperial College is concentrating on constraint based configuration of the proxylets. BT is investigating how to implement policy scripts as proxylets and to use genetic bacteria algorithms for deploying them in the network.
Fujitsu Laboratories, Japan funded project Pro-Active Role Based Management For Distributed Services is looking at roles as groups of policies applied to network management, and how constraints can be specified for these policies.
EPSRC Grant GR/L96103 SecPol: Specification and Analysis of Security Policy for Distributed Systems is investigating tools and techniques based on requirements engineering for refining high level goals into implementable policies.
EPSRC ROPA Grant GR/M/86019 PoNDS: A Generalised Policy Notation for Distributed Systems is developing the Ponder Language and applying it to Service Level Agreement specification.
EPSRC Grant GR/L24366 Effective Production of Parametrised FPGA Libraries results in a novel language and framework for developing reconfigurable hardware libraries, and various applications based on such libraries.
EPSRC Grant GR/L54356 Methods and Tools for Developing Reconfigurable Serial Designs is exploring a framework for combining reconfiguration and serialisation to enhance application adaptability, resource sharing and performance.
EPSRC ROPA Grant GR/L59658 Non-Standard Interpretation Techniques for Reconfigurable Hardware Design results in compile-time and run-time techniques for analysis and synthesis of reconfigurable hardware implementations.
Other Work on Policy
Most of the other work on policy language specification relates to security. Formal logic-based approaches such as ASL [24] and Ortalo [36] are generally difficult to use or understand, and do not easily map onto implementation mechanisms. The RBAC work [39] is also only related to security. There is also work within AT&T [16] and IBM [22] on Trust management policies to process queries of the form "does request r, supported by credential set C, comply with policy P?". The AT&T work has been used to specify trusted active network code. None of these includes the range of policies covered in Ponder, and most lack the flexibility of defining reusable composite policies supported by the object-oriented features of Ponder.
The standardisation work within the IETF Policy Group [23] concentrates on quality of service management and configuration within networks. They assume policies are objects stored in a directory service. A policy consumer (policy decision point – PDP) retrieves policies from the policy repository (e.g. LDAP server). A policy execution point (PEP) such as a router requests policy decisions using the Common Open Policy Service Protocol (COPS). The PEP enforces the policy for example by permitting/forbidding requests or allocating packets from a connection to a particular queue. A PEP and PDP could be combined into a single component. The IETF are defining a policy framework that can be used for classifying packet flows as well as specifying authorisations for network resources and services. They do not have a language for specifying policies but are using the X500 Directory schema [35]. IETF policies are of the form if (a set of conditions) then do (a set of actions). Directories are used for storing policies but not for grouping subjects and targets. They do not have concepts of subject and target that can be used to determine to which components a policy applies, so the mapping of policies to components has to be done by other means. A number of vendors are marketing policy toolkits for defining policies, related mostly to Quality of Service for network elements [6][19]. Most of these are similar to the IETF ideas but some also support specification of a security policy. None of them support a language but they do have graphical editors that allow administrators to define individual policies and then explicitly identify the enforcement components to which the policies must be loaded. None of these tools appear to have considered the automation of the policy lifecycle. Researchers at Bell Labs have developed a Policy Definition Language (PDL) which can be used to define policies of the form event causes action if condition [48] which are similar to the Ponder obligation policies. PDL does not support authorisation policies and has no support for composite policies.
Other policy work in the UK includes Prof. Pavlou’s group at the University of Surrey who has recently started working on policy management for differentiated services networks, and Drs. Bacon and Moody’s group at Cambridge University are working on policies for event based systems and role based access control.
Other Work on Reconfigurable Hardware Systems
Current work on reconfigurable hardware for networking applications has focused on providing efficient hardware solutions to specific tasks, particularly packet processing for routing or security purposes. We are not aware of research comparable to this proposal that spans multiple levels of network adaptability using policy based descriptions.
US activities on developing FPGA-based network processors include those at Department of Defence [33], Virginia Tech [19], Washington University [26] and Xilinx [15]. These processors are based on Xilinx FPGAs for frontend processing, such as packet filtering, distributed queuing and traffic shaping. Researchers at Pennsylvania [17] have developed a programmable protocol processing pipeline based on Altera devices; possible support for policy based operations is briefly mentioned. In the UK, EPSRC (GR/M29160) and BT are funding a project at Heriot-Watt and Edinburgh on using FPGAs for linking PCs connected by an optical local area network. Swedish researchers are studying FPGA-based content-addressable memory for internet protocol characterisation [14]. Asian researchers have also been active in reconfigurable systems for communication and network control [1]. Commercially, both Agere (www.agere.com, recently acquired by Lucent) and Cisco (www.cisco.com) use FPGAs extensively in their network processors. New reconfigurable processors dedicated to communications and networking applications (see www.chameleonsystems.com and www.siliconspice.com) are also available. All of the above, however, do not involve relating hardware implementations and high-level policy based network applications.
Turning now to design development, researchers are beginning to bridge the gap between applications and their hardware implementations. Researchers at Belfast [47], Brigham Young [21], Edinburgh [4], Strathclyde [38] and Xilinx [34] are working on methods and tools for reconfigurable designs. There has also been work on hardware accceleration of application packages, such as Matlab [3] and Photoshop [27]. However, none of the above projects is related to management of adaptive networks.
8 Relevance to Beneficiaries
There is considerable interest in policy based network management from service providers, network component vendors and computer system vendors (see www-dse.doc.ic.ac.uk/research/policies for links to sites working on policies). These organizations would benefit from a powerful language such as Ponder for specification of policies. Similarly vendors producing policy aware applications will need a language to specify policy. Research on hardware development will enable application developers to complete a design involving reconfigurable hardware more rapidly and more optimally than producing it by hand. While much of our work will be specific to network processor development, some of it will also contribute to reconfigurable hardware optimisation in general. We intend to make our tools and techniques available in the public domain for research purposes.
9 Exploitation and Dissemination
We have a good track record of publishing papers on our Policy work at major conferences and in journals. We will continue to publish. Prof. Sloman and Dr. Lupu have given tutorials on Policy specification, which includes details of the Imperial College work on Policy at NOMS'2000 and EDOC'2000. Another tutorial proposal has been submitted to IM'2001. As mentioned in section 1, the investigators have organized workshops on Policy in November 1999 and January 2001 to bring together members from various communities working on Policy specification, analysis and implementation (IETF, DMTF, Storage Network Industry Association [45], Role Based Access Control, Security Policy, Trust Management, Open Distributed Processing, Requirements Engineering etc.). John Strassner, our Cisco contact, chaired the IETF policy work and Andrea Westerinen (who works with John Strassner at Cisco) is one of the main architects of the CIM policy model. We are able to feed ideas into the standards work through these contacts.
We also have a good record of publishing our research on reconfigurable hardware design in major conferences (such as FPL and FCCM) and journals (such as IEE Proceedings, IEEE Computer, and IEEE Transactions on Computer-Aided Design). Should our research lead to exploitable results, we shall explore commercial opportunities with our collaborators such as Celoxica, Sony and Xilinx.
10 References
[5] Chen, F. and R.S. Sandhu. Constraints for Role-Based Access Control. In Proceedings of First ACM/NIST Role Based Access Control Workshop. 1995. Gaithersburg, Maryland, USA, ACM Press.
[6] Cisco Assure QoS Policy Manager http://www.cisco.com/warp/public/cc/cisco/mkt/enm/cap/index.shtml
[8] Corradi, A., R. Montanari, C. Stefanelli, E. Lupu and M. Sloman. Flexible Access Control for Java Mobile Code, 16th Annual Computer Security Applications Conference (ACSAC2000), Dec 2000, New Orleans USA.
[12] Dettmer, R. Software to Silicon. IEE Review, September 2000, pp. 15-19.
[13] Distributed Management Task Force, Inc. (DMTF), Common Information Model (CIM) Specification, version 2.2, available from http://www.dmtf.org/spec/cims.html, June 14, 1999.
[18] Haynes, S., J. Stone, P.Y.K. Cheung and W. Luk. Video Image Processing with the SONIC Architecture. IEEE Computer, April 2000, pp. 147-152.
[19] Hess, J.R. et. al. Implementation and Evaluation of a Prototype Reconfigurable Router. Proc. Int. Symp. FCCM, IEEE Computer Society Press, 1999, pp. 44-50.
[20] HP PolicyXpert http://www.openview.hp.com:80/products/policy/
[30] Lupu, E.C. and M. Sloman. Conflicts in Policy-Based Distributed Systems Management. IEEE Trans. on Software Engineering, 25(6): 852-869 Nov.1999.
[43] Sloman, M.S. Policy Driven Management for Distributed Systems. Journal of Network and Systems Management, 1994b. 2(4): 333-360.