|
Lecture Seven |
 |
|
Lecture Seven |
 |
| 7.1 Objectives |
This lecture covers basic system administration concepts and tasks, namely:
- The superuser root.
- Shutdown and system start-up.
- Adding users.
- Controlling user groups.
- Reconfiguring and recompiling the Linux kernel.
- Cron jobs.
- Keeping essential processes alive.
Note that you will not be given administrator access on the lab machines. However, you might like to try some basic administration tasks on your home PC.
| 7.2 The Superuser root |
The superuser is a privileged user who has unrestricted access to all commands and files on a system regardless of their permissions. The superuser's login is usually root. Access to the root account is restricted by a password (the root password). Because the root account has huge potential for destruction, the root password should be chosen carefully, only given to those who need it, and changed regularly.One way to become root is to log in as usual using the username root and the root password (usually security measures are in place so that this is only possible if you are using a "secure" console and not connecting over a network). Using root as your default login in this way is not recommended, however, because normal safeguards that apply to other user accounts do not apply to root. Consequently using root for mundane tasks often results in a memory lapse or misplaced keystrokes having catastrophic effects (e.g. forgetting for a moment which directory you are in and accidentally deleting another user's files, or accidentally typing "rm -rf * .txt" instead of "rm -rf *.txt" ).
A better way to become root is to use the su utility. su (switch user) lets you become another user (at least as far as the computer is concerned). If you don't specify the name of the user you wish to become, the system will assume you want to become root. Using su does not usually change your current directory, unless you specify a "-" option which will run the target user's startup scripts and change into their home directory (provided you can supply the right password of course). So:
$ su -
Password: xxxxxxxx
#Note that the root account often displays a different prompt (usually a #). To return to your old self, simply type "exit" at the shell prompt.
You should avoid leaving a root window open while you are not at your machine. Consider this paragraph from a humorous 1986 Computer Language article by Alan Filipski:
"The prudent administrator should be aware of common techniques used to breach UNIX security. The most widely known and practised attack on the security of the UNIX brand operating system is elegant in its simplicity. The perpetrator simply hangs around the system console until the operator leaves to get a drink or go to the bathroom. The intruder lunges for the console and types rm -rf / before anyone can pry his or her hands off the keyboard. Amateur efforts are characterised by typing in things such as ls or pwd. A skilled UNIX brand operating system security expert would laugh at such attempts."
| 7.3 Shutdown and System Start-up |
- Shutdown: shutdown, halt, reboot (in /sbin)
/sbin/shutdown allows a UNIX system to shut down gracefully and securely. All logged-in users are notified that the system is going down, and new logins are blocked. It is possible to shut the system down immediately or after a specified delay and to specify what should happen after the system has been shut down:# /sbin/shutdown -r now
(shut down now and reboot)
# /sbin/shutdown -h +5(shut down in 5 minutes & halt)
# /sbin/shutdown -k 17:00(fake a shutdown at 5pm)
halt and reboot are equivalent to shutdown -h and shutdown -r respectively.
If you have to shut a system down extremely urgently or for some reason cannot use shutdown, it is at least a good idea to first run the command:
# sync
which forces the state of the file system to be brought up to date.
- System startup:
At system startup, the operating system performs various low-level tasks, such as initialising the memory system, loading up device drivers to communicate with hardware devices, mounting filesystems and creating the init process (the parent of all processes). init's primary responsibility is to start up the system services as specified in /etc/inittab. Typically these services include gettys (i.e. virtual terminals where users can login), and the scripts in the directory /etc/rc.d/init.d which usually spawn high-level daemons such as httpd (the web server). On most UNIX systems you can type dmesg to see system startup messages, or look in /var/log/messages.
If a mounted filesystem is not "clean" (e.g. the machine was turned off without shutting down properly), a system utility fsck is automatically run to repair it. Automatic running can only fix certain errors, however, and you may have to run it manually:
# fsck filesys
where filesys is the name of a device (e.g. /dev/hda1) or a mount point (like /). "Lost" files recovered during this process end up in the lost+found directory. Some more modern filesystems called "journaling" file systems don't require fsck, since they keep extensive logs of filesystem events and are able to recover in a similar way to a transactional database.
| 7.4 Adding Users |
- useradd (in /usr/sbin):
useradd is a utility for adding new users to a UNIX system. It adds new user information to the /etc/passwd file and creates a new home directory for the user. When you add a new user, you should also set their password (using the -p option on useradd, or using the passwd utility):
# useradd bob
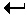
# passwd bob
| 7.5 Controlling User Groups |
- groupadd (in /usr/sbin):
groupadd creates a new user group and adds the new information to /etc/group:
# groupadd groupname
- usermod (in /usr/sbin):
Every user belongs to a primary group and possibly also to a set of supplementary groups. To modify the group permissions of an existing user, use
# usermod -g initialgroup username -G othergroups
where othergroups is a list of supplementary group names separated by commas (with no intervening whitespace).
- groups
You can find out which groups a user belongs to by typing:
# groups username
| 7.6 Reconfiguring and Recompiling the Linux Kernel |
Linux has a modular, customisable kernel with several switchable options (e.g. support for multiple processors and device drivers for various hardware devices). It may happen that some new hardware is added to a Linux machine which requires you to recompile the kernel so that it includes device driver support (and possibly new system calls) for the new hardware. To do this, you will need to rebuild the Linux kernel from scratch as follows:
- Look in /usr/src/linux for the kernel source code. If it isn't there (or if there is just a message saying that only kernel binaries have been installed), get hold of a copy of the latest kernel source code from http://www.kernel.org and untar it into /usr/src/linux.
- Change directory to /usr/src/linux.
- To configure the kernel type either
# make config (simple text mode configuration), or
# make menuconfig (menu-driven text configuration), or
# make xconfig (graphical configuration for X)You will be asked to select which modules (device drivers, multiprocessor support etc.) you wish to include. For each module, you can chose to include it in the kernel code (y), incorporate it as an optional module that will be loaded if needed (m) or to exclude it from the kernel code (n). To find out which optional modules have actually been loaded you can run lsmod when the system reboots.
- Now type:
# make dep (to build source code dependencies)
# make clean (to delete all stale object files)
# make bzImage (to build the new kernel)
# make modules (to build the new optional modules)
# make modules_install (to install the modules)The file /usr/src/linux/arch/i386/boot/bzImage now contains your new kernel image. It remains only to install it.
- Change directory to /usr/src/linux/arch/i386/boot. In the same directory should be a script called install.sh which will copy your kernel image into /boot/vmlinuz:
# install.sh version bzImage /boot/System.map /boot
where version is the kernel version number (of form 2.2.xx).
- Finally, you may need to update the /etc/lilo.conf file so that lilo (the Linux boot loader) includes an entry for your new kernel. Then run
# lilo
to update the changes. When you reboot your machine, you should be able to select your new kernel image from the lilo boot loader.
| 7.7 Cron Jobs |
crond is a daemon that executes commands that need to be run regularly according to some schedule. The schedule and corresponding commands are stored in the file /etc/crontab.Each entry in the /etc/crontab file entry contains six fields separated by spaces or tabs in the following form:
minute hour day_of_month month weekday command
These fields accept the following values:
minute 0 through 59
hour 0 through 23
day_of_month 1 through 31
month 1 through 12
weekday 0 (Sun) through 6 (Sat)
command a shell commandYou must specify a value for each field. Except for the command field, these fields can contain the following:
You can also specify some execution environment options at the top of the /etc/crontab file:
- A number in the specified range, e.g. to run a command in May, specify 5 in the month field.
- Two numbers separated by a dash to indicate an inclusive range, e.g. to run a cron job on Tuesday through Friday, place 2-5 in the weekday field.
- A list of numbers separated by commas, e.g. to run a command on the first and last day of January, you would specify 1,31 in the day_of_month field.
- * (asterisk), meaning all allowed values, e.g. to run a job every hour, specify an asterisk in the hour field.
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
MAILTO=rootTo run the calendar command at 6:30am. every Mon, Wed, and Fri, a suitable /etc/crontab entry would be:
30 6 * * 1,3,5 /usr/bin/calendar
The output of the command will be mailed to the user specified in the MAILTO environment option.
You don't need to restart the cron daemon crond after changing /etc/crontab - it automatically detects changes.
| 7.8 Keeping Essential Processes Alive |
It is important that daemons related to mission critical services are immediately respawned if they fail for some reason. You can do this by adding your own entries to the /etc/inittab file. For example:rs:2345:respawn:/home/sms/server/RingToneServer
Here rs is a 2 character code identifying the service, and 2345 are the runlevels (to find about runlevels, type man runlevel) for which the process should be created. The init process will create the RingToneServer process at system startup, and respawn it should it die for any reason.